There are dozens of protocols used in the ICS domain. Many of these protocols were developed to support a specific technology, and as such, are uncommon or only applicable to a single vendor. Some ICS devices are old—they can be in use 25 or 30 years—and use proprietary protocols developed by vendors that are no longer in business. The owners of these systems often resort to buying used equipment to keep their systems operational.
Most, if not all, common ICS protocols are openly published and available for review. The protocols are typically transmitted in clear text, meaning they are not encrypted. This makes them easy targets for eavesdropping and subject to man-in-the-middle (MiTM) attacks. Many of the older protocols were adapted for a network environment by “wrapping” them in TCP/IP packets. This does not improve security because TCP/IP is not a secure protocol.
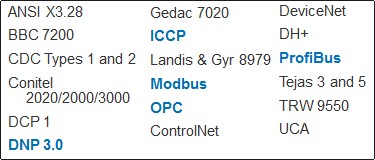
The ICS vendor community has been under pressure by the ICS owner/operator community to move toward greater inter-operability, and toward a more common set of protocols for communications. Unfortunately, many of these protocols are not secure by design—they were designed for reliability. Protocols highlighted in blue are the most common and will be discussed in the following slides.
Copyright: Cybersecurity & Infrastructure Security Agency (CISA)
